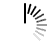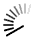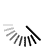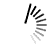Splunk - Field Searching
When Splunk reads the uploaded machine data, it interprets the data and divides it into many fields which represent a single logical fact about the entire data record. For example, a single record of information may contain server name, timestamp of the event, type of the event being logged whether login attempt or a http response etc. Even in case of unstructured data Splunk tries to divide the fields into key value pairs or separate them based on the data types they have, like numeric and string etc.
Continuing with the data uploaded in the previous chapter we can see the fields from the secure.log file by clicking on the show fields link which will open up the following screen. We can notice the fields Splunk has generated from this log file.
Choosing the Fields
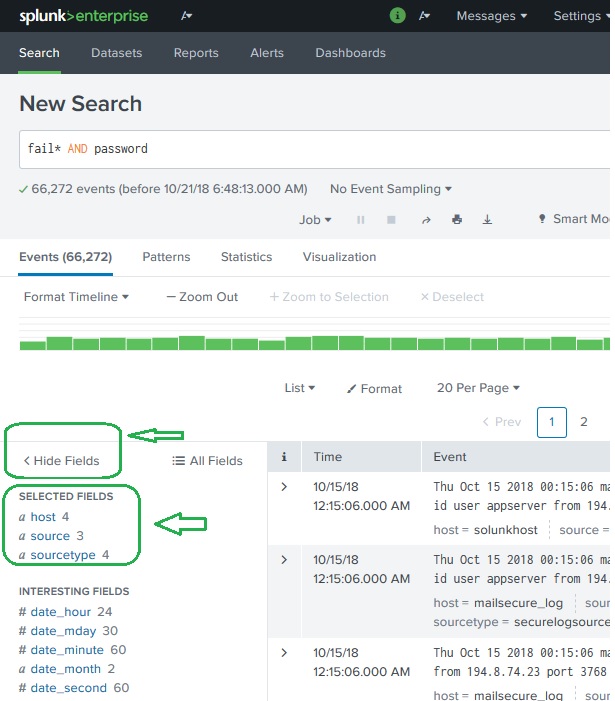
We can choose what fields to be displayed by selecting or unselecting the fields from the list of all fields. We click on the link all fields and it open a window showing the list of all the fields. Some of these fields have check marks against them showing they are already selected. We can use the check boxes to choose our fields for display.
Besides the name of the filed it displays the number of distinct values the fields have, its data type and what percentage of events this filed is present in.
Field Summary
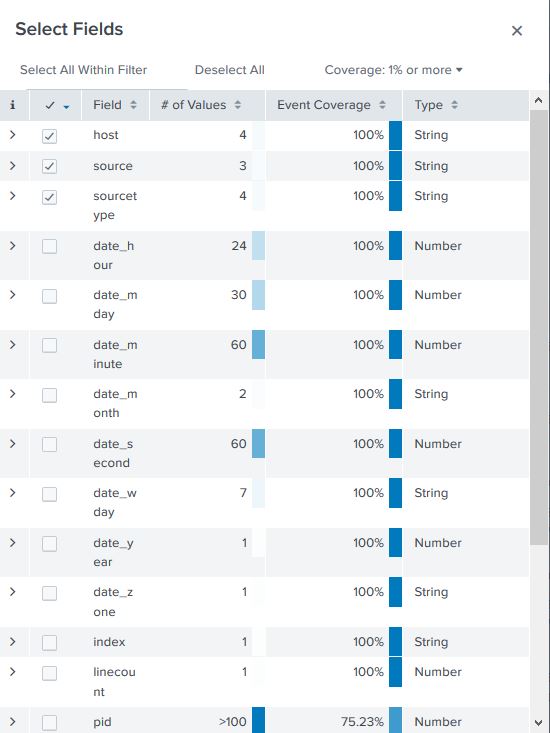
A very detailed stats for every selected field become available by clicking on the name of the field. It shows all the distinct values for the field, their count and their percentages.
Using Fields in Search
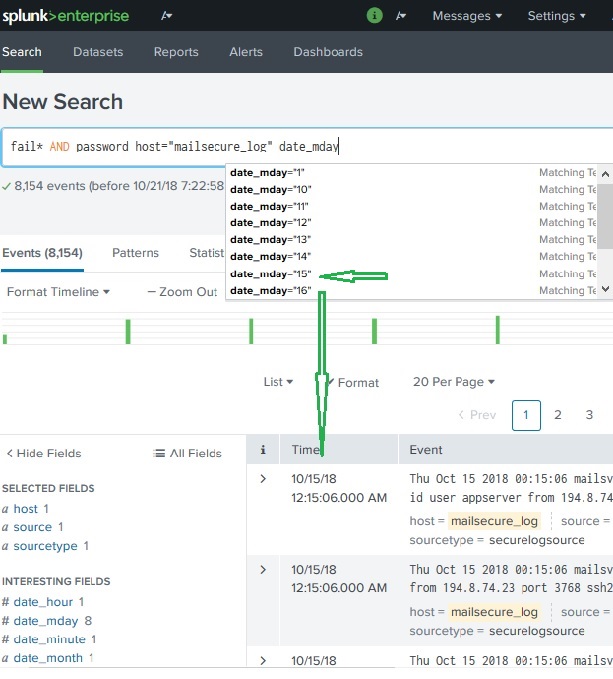
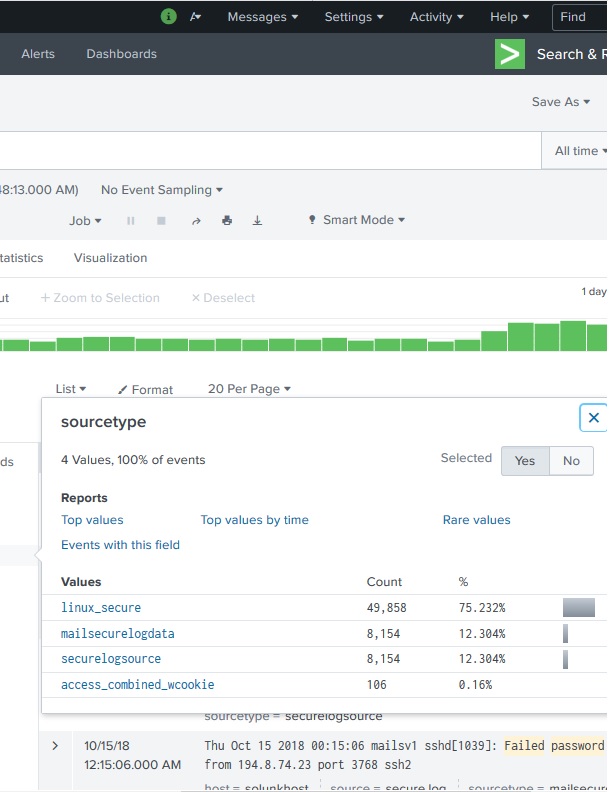
The filed names can also be inserted into the search box along with the specific values for the search. In the below example we aim to find all the records for the date 15th Oct for the host named mailsecure_log. We get the result for this specific date.