Splunk - Time Range Search
The Splunk web interface displays timeline which indicates the distribution of events over a range of time. There are preset time intervals from which you can select a specific time range, or you can customize the time range to your need. The below screen shows the various preset timeline options. Choosing any of this option will fetch the data for only that specific time period which you can also analyze further using the custom timeline options available.
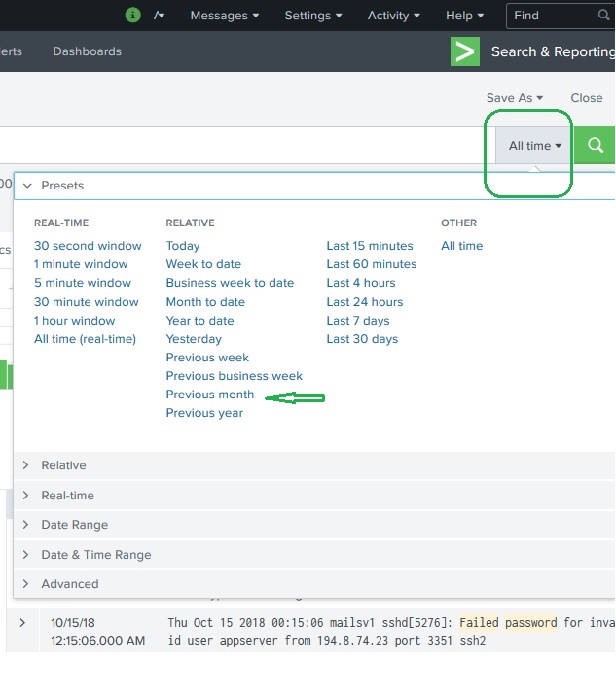
For example, choosing the previous month option gives us the result only for the previous month as you can see the in spread of the timeline graph below.
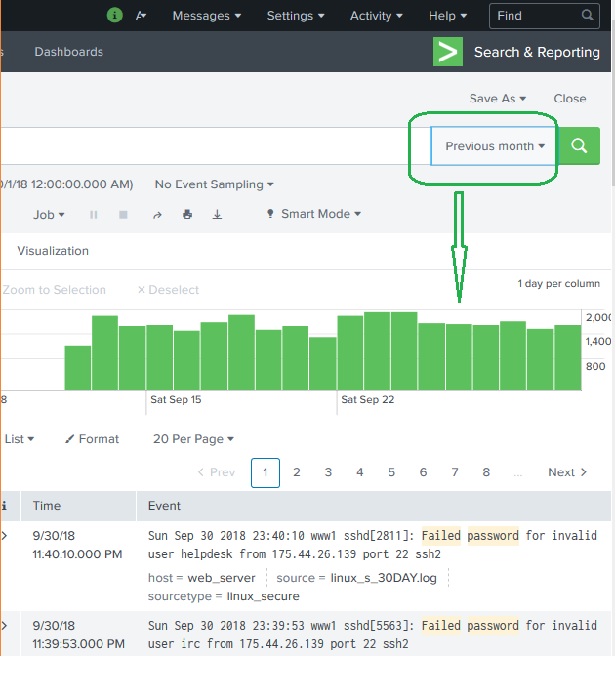
Selecting a Time Subset
By clicking and dragging across the bars in the timeline we can select a subset of the result that already exists. This does not cause the re-execution of the query. It only filters out the records from the existing result set.
Below is the diagram which shows the selection of a subset from the result set.
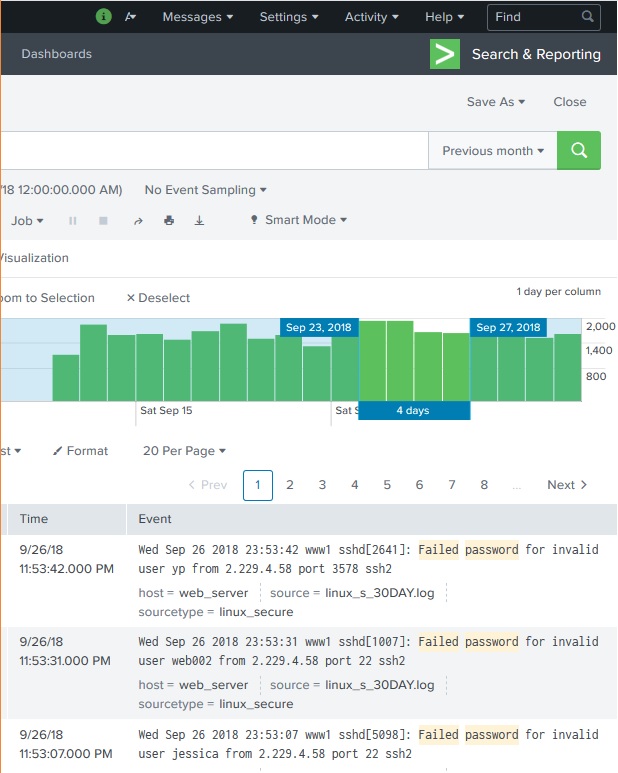
Earliest and Latest
The two commands, earliest and latest can be used in the search bar to indicate the time range in between which you filter out the results. It is similar to selecting the time subset, but it is through commands rather than the option of clicking at a specific time line bar. So, it provides a finer control over that data range you can pick for your analysis.
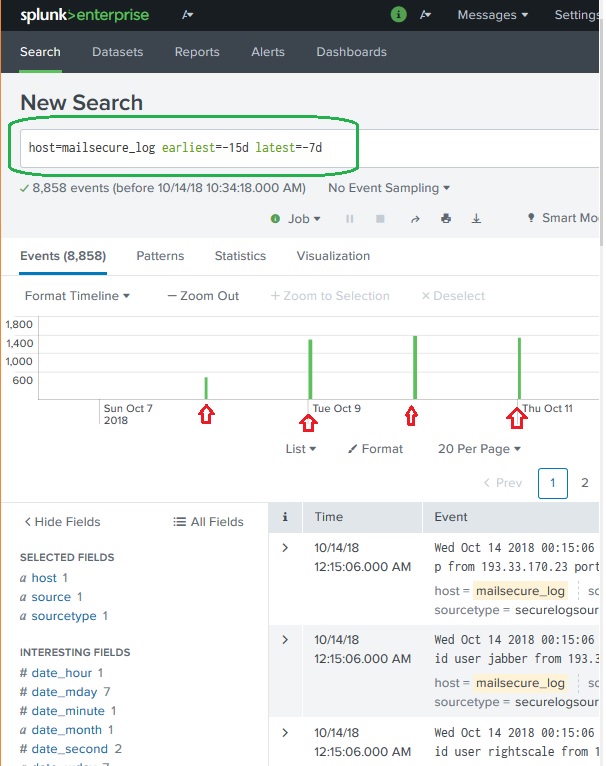
In the above diagram we give a time range between last 7 days to last 15 days. So, the data in between these two days is displayed.
Nearby Events
We can also find near by events of a specific time by mentioning how close we want the events to be filtered out. We have the option of choosing the scale of the interval, like – seconds, minutes, days and week etc.