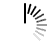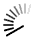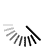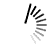Splunk - Tags
Tags are used to assign names to specific field and value combinations. These fields can be event type, host, source, or source type etc. You can also use a tag to group a set of field values together, so that you can search for them with one command. For example, you can tag all the different files generated on a Monday to a tag named mon_files.
To find the field-value pair which we are going to tag, we need to expand the events and locate the field to be considered. The below diagram shows how we can expand an event to see the fields.
Creating Tags
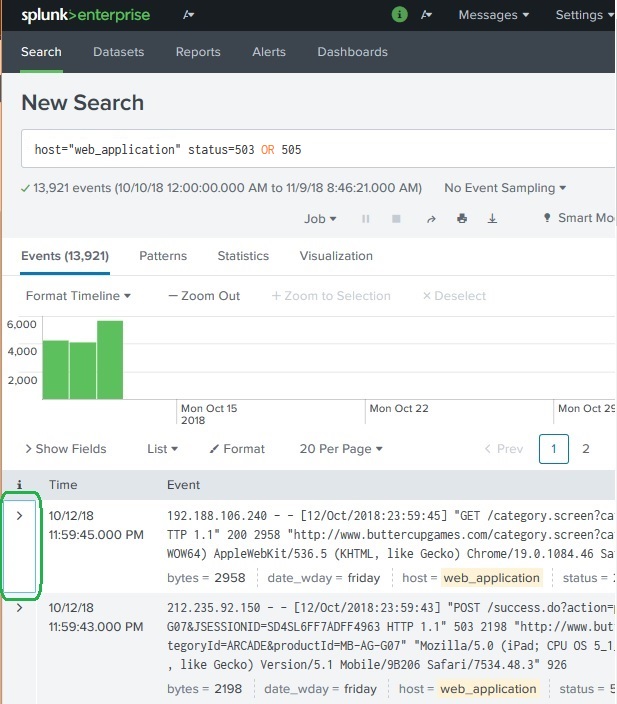
We can create tags by adding the tag value to the field-value pair using Edit Tags option as shown below. We choose the field and under the Actions column choose this option.
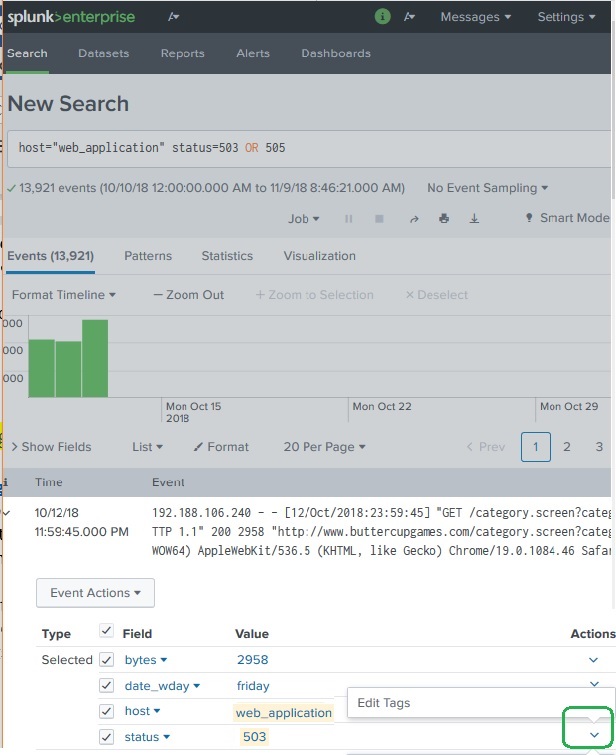
The next screen prompts us to define the tag. For the Status field we choose the status value of 503 or 505 and assign a tag named server_error as shown below. We have to do it one by one by choosing two events, each with the events with status value 503 and 505. The diagram below shows the method for status value as 503. We have to repeat the same steps for an event with status value as 505.
Searching Using Tags
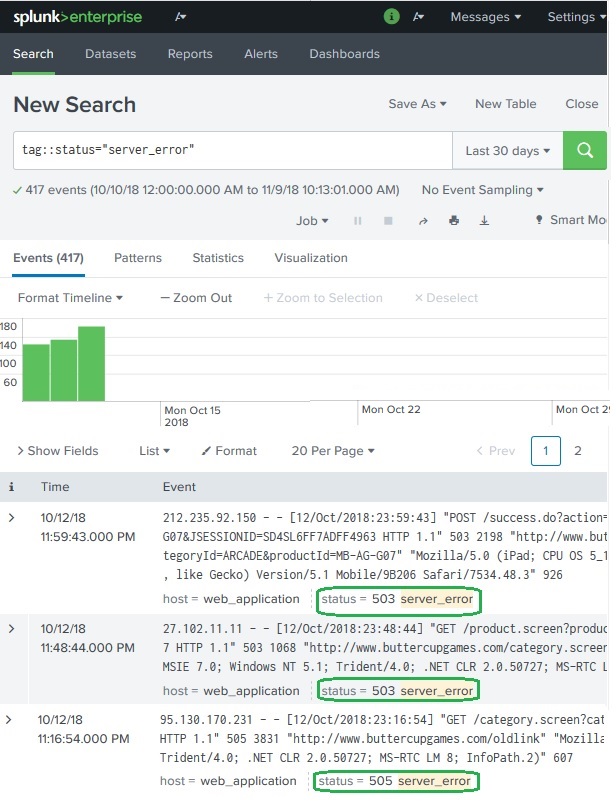
Once the tags are created, we can search for events containing the Tag by simply writing the Tag name in the search bar. In the below diagram we see all the events which have status as 503 or 505.